Programs
The defining feature of modern computers which distinguishes them from all other machines is that they can be
programmed. That is to say that some type of
instructions (the
program) can be given to the computer, and it will carry process them. While some computers may have strange concepts "instructions" and "output" (see
quantum computing), modern computers based on the
von Neumann architecture often have machine code in the form of an
imperative programming language.
In practical terms, a
computer program may be just a few instructions or extend to many millions of instructions, as do the programs for
word processors and
web browsers for example. A typical modern computer can execute billions of instructions per second (
gigaflops) and rarely makes a mistake over many years of operation. Large computer programs consisting of several million instructions may take teams of
programmers years to write, and due to the complexity of the task almost certainly contain errors.
Stored program architecture

A 1970s
punched card containing one line from a
FORTRAN program. The card reads: "Z(1) = Y + W(1)" and is labelled "PROJ039" for identification purposes.
This section applies to most common
RAM machine-based computers.
In most cases, computer instructions are simple: add one number to another, move some data from one location to another, send a message to some external device, etc. These instructions are read from the computer's
memory and are generally carried out (
executed) in the order they were given. However, there are usually specialized instructions to tell the computer to jump ahead or backwards to some other place in the program and to carry on executing from there. These are called "jump" instructions (or
branches). Furthermore, jump instructions may be made to happen
conditionally so that different sequences of instructions may be used depending on the result of some previous calculation or some external event. Many computers directly support
subroutines by providing a type of jump that "remembers" the location it jumped from and another instruction to return to the instruction following that jump instruction.
Program execution might be likened to reading a book. While a person will normally read each word and line in sequence, they may at times jump back to an earlier place in the text or skip sections that are not of interest. Similarly, a computer may sometimes go back and repeat the instructions in some section of the program over and over again until some internal condition is met. This is called the
flow of control within the program and it is what allows the computer to perform tasks repeatedly without human intervention.
Comparatively, a person using a pocket
calculator can perform a basic arithmetic operation such as adding two numbers with just a few button presses. But to add together all of the numbers from 1 to 1,000 would take thousands of button presses and a lot of time—with a near certainty of making a mistake. On the other hand, a computer may be programmed to do this with just a few simple instructions. For example:
mov #0, sum ; set sum to 0
mov #1, num ; set num to 1
loop: add num, sum ; add num to sum
add #1, num ; add 1 to num
cmp num, #1000 ; compare num to 1000
ble loop ; if num <= 1000, go back to 'loop'
halt ; end of program. stop running
Once told to run this program, the computer will perform the repetitive addition task without further human intervention. It will almost never make a mistake and a modern PC can complete the task in about a millionth of a second.
[32]
Bugs
Main article:
software bug
The actual first computer bug, a moth found trapped on a relay of the Harvard Mark II computer
Errors in computer programs are called "
bugs". Bugs may be benign and not affect the usefulness of the program, or have only subtle effects. But in some cases they may cause the program - or the entire system - to "
hang"—become unresponsive to input such as
mouse clicks or keystrokes, or to completely fail or "
crash". Otherwise benign bugs may sometimes be harnessed for malicious intent by an unscrupulous user writing an "
exploit"—code designed to take advantage of a bug and disrupt a computer's proper execution. Bugs are usually not the fault of the computer. Since computers merely execute the instructions they are given, bugs are nearly always the result of programmer error or an oversight made in the program's design.
[33]
Rear Admiral Grace Hopper is credited for having first used the term 'bugs' in computing after a dead moth was found shorting a relay of the
Harvard Mark II computer in September 1947.
[34]
Machine code
In most computers, individual instructions are stored as
machine code with each instruction being given a unique number (its operation code or
opcode for short). The command to add two numbers together would have one opcode, the command to multiply them would have a different opcode and so on. The simplest computers are able to perform any of a handful of different instructions; the more complex computers have several hundred to choose from—each with a unique numerical code. Since the computer's memory is able to store numbers, it can also store the instruction codes. This leads to the important fact that entire programs (which are just lists of these instructions) can be represented as lists of numbers and can themselves be manipulated inside the computer in the same way as numeric data. The fundamental concept of storing programs in the computer's memory alongside the data they operate on is the crux of the von Neumann, or stored program, architecture. In some cases, a computer might store some or all of its program in memory that is kept separate from the data it operates on. This is called the
Harvard architecture after the
Harvard Mark I computer. Modern von Neumann computers display some traits of the Harvard architecture in their designs, such as in
CPU caches.
While it is possible to write computer programs as long lists of numbers (
machine language) and while this technique was used with many early computers,
[35] it is extremely tedious and potentially error-prone to do so in practice, especially for complicated programs. Instead, each basic instruction can be given a short name that is indicative of its function and easy to remember—a
mnemonic such as ADD, SUB, MULT or JUMP. These mnemonics are collectively known as a computer's
assembly language. Converting programs written in assembly language into something the computer can actually understand (machine language) is usually done by a computer program called an assembler. Machine languages and the assembly languages that represent them (collectively termed
low-level programming languages) tend to be unique to a particular type of computer. For instance, an
ARM architecture computer (such as may be found in a
PDA or a
hand-held videogame) cannot understand the machine language of an
Intel Pentium or the
AMD Athlon 64 computer that might be in a
PC.
[36]
Higher-level languages and program design
Though considerably easier than in machine language, writing long programs in assembly language is often difficult and is also error prone. Therefore, most practical programs are written in more abstract
high-level programming languages that are able to express the needs of the
programmer more conveniently (and thereby help reduce programmer error). High level languages are usually "compiled" into machine language (or sometimes into assembly language and then into machine language) using another computer program called a
compiler.
[37] High level languages are less related to the workings of the target computer than assembly language, and more related to the language and structure of the problem(s) to be solved by the final program. It is therefore often possible to use different compilers to translate the same high level language program into the machine language of many different types of computer. This is part of the means by which software like video games may be made available for different computer architectures such as personal computers and various
video game consoles.
The task of developing large
software systems presents a significant intellectual challenge. Producing software with an acceptably high reliability within a predictable schedule and budget has historically been difficult; the academic and professional discipline of
software engineering concentrates specifically on this challenge.
Function
A general purpose computer has four main components: the
arithmetic logic unit (ALU), the
control unit, the
memory, and the input and output devices (collectively termed I/O). These parts are interconnected by
busses, often made of groups of
wires.
Inside each of these parts are thousands to trillions of small
electrical circuits which can be turned off or on by means of an
electronic switch. Each circuit represents a
bit (binary digit) of information so that when the circuit is on it represents a "1", and when off it represents a "0" (in positive logic representation). The circuits are arranged in
logic gates so that one or more of the circuits may control the state of one or more of the other circuits.
The control unit, ALU, registers, and basic I/O (and often other hardware closely linked with these) are collectively known as a
central processing unit (CPU). Early CPUs were composed of many separate components but since the mid-1970s CPUs have typically been constructed on a single
integrated circuit called a
microprocessor.
Control unit
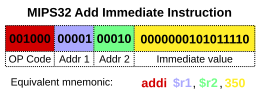
Diagram showing how a particular
MIPS architecture instruction would be decoded by the control system.
The control unit (often called a control system or central controller) manages the computer's various components; it reads and interprets (decodes) the program instructions, transforming them into a series of control signals which activate other parts of the computer.
[38] Control systems in advanced computers may change the order of some instructions so as to improve performance.
A key component common to all CPUs is the
program counter, a special memory cell (a
register) that keeps track of which location in memory the next instruction is to be read from.
[39]
The control system's function is as follows—note that this is a simplified description, and some of these steps may be performed concurrently or in a different order depending on the type of CPU:
- Read the code for the next instruction from the cell indicated by the program counter.
- Decode the numerical code for the instruction into a set of commands or signals for each of the other systems.
- Increment the program counter so it points to the next instruction.
- Read whatever data the instruction requires from cells in memory (or perhaps from an input device). The location of this required data is typically stored within the instruction code.
- Provide the necessary data to an ALU or register.
- If the instruction requires an ALU or specialized hardware to complete, instruct the hardware to perform the requested operation.
- Write the result from the ALU back to a memory location or to a register or perhaps an output device.
- Jump back to step (1).
Since the program counter is (conceptually) just another set of memory cells, it can be changed by calculations done in the ALU. Adding 100 to the program counter would cause the next instruction to be read from a place 100 locations further down the program. Instructions that modify the program counter are often known as "jumps" and allow for loops (instructions that are repeated by the computer) and often conditional instruction execution (both examples of
control flow).
It is noticeable that the sequence of operations that the control unit goes through to process an instruction is in itself like a short computer program—and indeed, in some more complex CPU designs, there is another yet smaller computer called a
microsequencer that runs a
microcode program that causes all of these events to happen.
Arithmetic/logic unit (ALU)
The ALU is capable of performing two classes of operations: arithmetic and logic.
[40]
The set of arithmetic operations that a particular ALU supports may be limited to adding and subtracting or might include multiplying or dividing,
trigonometry functions (sine, cosine, etc.) and
square roots. Some can only operate on whole numbers (
integers) whilst others use
floating point to represent
real numbers—albeit with limited precision. However, any computer that is capable of performing just the simplest operations can be programmed to break down the more complex operations into simple steps that it can perform. Therefore, any computer can be programmed to perform any arithmetic operation—although it will take more time to do so if its ALU does not directly support the operation. An ALU may also compare numbers and return
boolean truth values (true or false) depending on whether one is equal to, greater than or less than the other ("is 64 greater than 65?").
Logic operations involve
Boolean logic:
AND,
OR,
XOR and
NOT. These can be useful both for creating complicated
conditional statements and processing
boolean logic.
Superscalar computers may contain multiple ALUs so that they can process several instructions at the same time.
[41] Graphics processors and computers with
SIMD and
MIMD features often provide ALUs that can perform arithmetic on
vectors and
matrices.
Memory

Magnetic core memory was the computer memory of choice throughout the 1960s, until it was replaced by semiconductor memory.
A computer's memory can be viewed as a list of cells into which numbers can be placed or read. Each cell has a numbered "address" and can store a single number. The computer can be instructed to "put the number 123 into the cell numbered 1357" or to "add the number that is in cell 1357 to the number that is in cell 2468 and put the answer into cell 1595". The information stored in memory may represent practically anything. Letters, numbers, even computer instructions can be placed into memory with equal ease. Since the CPU does not differentiate between different types of information, it is the software's responsibility to give significance to what the memory sees as nothing but a series of numbers.
In almost all modern computers, each memory cell is set up to store
binary numbers in groups of eight bits (called a
byte). Each byte is able to represent 256 different numbers (2^8 = 256); either from 0 to 255 or −128 to +127. To store larger numbers, several consecutive bytes may be used (typically, two, four or eight). When negative numbers are required, they are usually stored in
two's complement notation. Other arrangements are possible, but are usually not seen outside of specialized applications or historical contexts. A computer can store any kind of information in memory if it can be represented numerically. Modern computers have billions or even trillions of bytes of memory.
The CPU contains a special set of memory cells called
registers that can be read and written to much more rapidly than the main memory area. There are typically between two and one hundred registers depending on the type of CPU. Registers are used for the most frequently needed data items to avoid having to access main memory every time data is needed. As data is constantly being worked on, reducing the need to access main memory (which is often slow compared to the ALU and control units) greatly increases the computer's speed.
Computer main memory comes in two principal varieties:
random-access memory or RAM and
read-only memory or ROM. RAM can be read and written to anytime the CPU commands it, but ROM is pre-loaded with data and software that never changes, so the CPU can only read from it. ROM is typically used to store the computer's initial start-up instructions. In general, the contents of RAM are erased when the power to the computer is turned off, but ROM retains its data indefinitely. In a PC, the ROM contains a specialized program called the
BIOS that orchestrates loading the computer's
operating system from the hard disk drive into RAM whenever the computer is turned on or reset. In
embedded computers, which frequently do not have disk drives, all of the required software may be stored in ROM. Software stored in ROM is often called
firmware, because it is notionally more like hardware than software.
Flash memory blurs the distinction between ROM and RAM, as it retains its data when turned off but is also rewritable. It is typically much slower than conventional ROM and RAM however, so its use is restricted to applications where high speed is unnecessary.
[42]
In more sophisticated computers there may be one or more RAM
cache memories which are slower than registers but faster than main memory. Generally computers with this sort of cache are designed to move frequently needed data into the cache automatically, often without the need for any intervention on the programmer's part.
Input/output (I/O)
Main article:
Input/outputI/O is the means by which a computer exchanges information with the outside world.
[43] Devices that provide input or output to the computer are called
peripherals.
[44] On a typical
personal computer, peripherals include input devices like the keyboard and
mouse, and output devices such as the
display and
printer.
Hard disk drives,
floppy disk drives and
optical disc drives serve as both input and output devices.
Computer networking is another form of I/O.
Often, I/O devices are complex computers in their own right with their own CPU and memory. A
graphics processing unit might contain fifty or more tiny computers that perform the calculations necessary to display
3D graphics[citation needed]. Modern
desktop computers contain many smaller computers that assist the main CPU in performing I/O.
Multitasking
While a computer may be viewed as running one gigantic program stored in its main memory, in some systems it is necessary to give the appearance of running several programs simultaneously. This is achieved by multitasking i.e. having the computer switch rapidly between running each program in turn.
[45]
One means by which this is done is with a special signal called an
interrupt which can periodically cause the computer to stop executing instructions where it was and do something else instead. By remembering where it was executing prior to the interrupt, the computer can return to that task later. If several programs are running "at the same time", then the interrupt generator might be causing several hundred interrupts per second, causing a program switch each time. Since modern computers typically execute instructions several orders of magnitude faster than human perception, it may appear that many programs are running at the same time even though only one is ever executing in any given instant. This method of multitasking is sometimes termed "time-sharing" since each program is allocated a "slice" of time in turn.
[46]
Before the era of cheap computers, the principal use for multitasking was to allow many people to share the same computer.
Seemingly, multitasking would cause a computer that is switching between several programs to run more slowly — in direct proportion to the number of programs it is running. However, most programs spend much of their time waiting for slow input/output devices to complete their tasks. If a program is waiting for the user to click on the mouse or press a key on the keyboard, then it will not take a "time slice" until the event it is waiting for has occurred. This frees up time for other programs to execute so that many programs may be run at the same time without unacceptable speed loss.
Multiprocessing

Cray designed many supercomputers that used multiprocessing heavily.
Some computers are designed to distribute their work across several CPUs in a multiprocessing configuration, a technique once employed only in large and powerful machines such as
supercomputers,
mainframe computers and
servers. Multiprocessor and
multi-core (multiple CPUs on a single integrated circuit) personal and laptop computers are now widely available, and are being increasingly used in lower-end markets as a result.
Supercomputers in particular often have highly unique architectures that differ significantly from the basic stored-program architecture and from general purpose computers.
[47] They often feature thousands of CPUs, customized high-speed interconnects, and specialized computing hardware. Such designs tend to be useful only for specialized tasks due to the large scale of program organization required to successfully utilize most of the available resources at once. Supercomputers usually see usage in large-scale
simulation,
graphics rendering, and
cryptography applications, as well as with other so-called "
embarrassingly parallel" tasks.
Networking and the Internet
Computers have been used to coordinate information between multiple locations since the 1950s. The U.S. military's
SAGE system was the first large-scale example of such a system, which led to a number of special-purpose commercial systems like
Sabre.
[48]
In the 1970s, computer engineers at research institutions throughout the United States began to link their computers together using telecommunications technology. This effort was funded by ARPA (now
DARPA), and the
computer network that it produced was called the
ARPANET.
[49] The technologies that made the Arpanet possible spread and evolved.
In time, the network spread beyond academic and military institutions and became known as the
Internet. The emergence of networking involved a redefinition of the nature and boundaries of the computer. Computer operating systems and applications were modified to include the ability to define and access the resources of other computers on the network, such as peripheral devices, stored information, and the like, as extensions of the resources of an individual computer. Initially these facilities were available primarily to people working in high-tech environments, but in the 1990s the spread of applications like
e-mail and the
World Wide Web, combined with the development of cheap, fast networking technologies like
Ethernet and
ADSL saw computer networking become almost ubiquitous. In fact, the number of computers that are networked is growing phenomenally. A very large proportion of
personal computers regularly connect to the
Internet to communicate and receive information. "Wireless" networking, often utilizing
mobile phone networks, has meant networking is becoming increasingly ubiquitous even in mobile computing environments.
Misconceptions
A computer does not need to be
electric, nor even have a
processor, nor
RAM, nor even
hard disk. The minimal definition of a computer is anything that transforms
information in a purposeful way.
[citation needed] However the traditional definition of a computer is a device having memory, mass storage, processor (CPU), and Input & Output devices.
[50] Anything less would be a simple processor.
Required technology
Computational systems as
flexible as a
personal computer can be built out of almost anything. For example, a computer can be made out of
billiard balls (
billiard ball computer); this is an unintuitive and pedagogical example that a computer can be made out of almost anything. More realistically, modern computers are made out of
transistors made of
photolithographed semiconductors.
Historically, computers evolved from
mechanical computers and eventually from
vacuum tubes to transistors.
There is active research to make computers out of many promising new types of technology, such as
optical computing,
DNA computers,
neural computers, and
quantum computers. Some of these can easily tackle problems that modern computers cannot (such as how quantum computers can break some modern encryption algorithms by
quantum factoring).
Computer architecture paradigms
Some different
paradigms of how to build a computer from the ground-up:
- RAM machines
- These are the types of computers with a CPU, computer memory, etc., which understand basic instructions in a machine language. The concept evolved from the Turing machine.
- Brains
- Brains are massively parallel processors made of neurons, wired in intricate patterns, that communicate via electricity and neurotransmitter chemicals.
- Programming languages
- Such as the lambda calculus, or modern programming languages, are virtual computers built on top of other computers.
- Cellular automata
- For example, the game of Life can create "gliders" and "loops" and other constructs that transmit information; this paradigm can be applied to DNA computing, chemical computing, etc.
- Groups and committees
- The linking of multiple computers (brains) is itself a computer
Logic gates are a common abstraction which can apply to most of the above
digital or
analog paradigms.
The ability to store and execute lists of instructions called
programs makes computers extremely versatile, distinguishing them from
calculators. The
Church–Turing thesis is a mathematical statement of this versatility: any computer with a
minimum capability (being Turing-complete) is, in principle, capable of performing the same tasks that any other computer can perform. Therefore any type of computer (
netbook,
supercomputer,
cellular automaton, etc.) is able to perform the same computational tasks, given enough time and storage capacity.
Limited-function computers
Conversely, a computer which is limited in function (one that is not "
Turing-complete") cannot simulate arbitrary things. For example, simple
four-function calculators cannot simulate a real computer without human intervention. As a more complicated example, without the ability to
program a
gaming console, it can never accomplish what a programmable calculator from the 1990s could (given enough time); the system as a whole is not Turing-complete, even though it contains a Turing-complete component (the microprocessor). Living organisms (the body, not the brain) are also limited-function computers designed to make copies of themselves; they cannot be reprogrammed without
genetic engineering.
Virtual computers
A "computer" is commonly considered to be a physical device. However, one can create a computer program which describes how to run a different computer, i.e. "simulating a computer in a computer". Not only is this a
constructive proof of the
Church-Turing thesis, but is also extremely common in all modern computers. For example, some
programming languages use something called an
interpreter, which is a simulated computer built on top of the basic computer; this allows programmers to write
code (computer input) in a different language than the one understood by the base computer (the alternative is to use a
compiler). Additionally,
virtual machines are simulated computers which virtually replicate a physical computer in software, and are very commonly used by
IT.
Virtual machines are also a common technique used to create
emulators, such
game console emulators.
Further topics
Artificial intelligence
A computer will solve problems in exactly the way they are programmed to, without regard to efficiency nor alternative solutions nor possible shortcuts nor possible errors in the code. Computer programs which learn and adapt are part of the emerging field of
artificial intelligence and
machine learning.
Hardware
The term
hardware covers all of those parts of a computer that are tangible objects. Circuits, displays, power supplies, cables, keyboards, printers and mice are all hardware.
History of computing hardware
| First Generation (Mechanical/Electromechanical) | Calculators | Antikythera mechanism, Difference engine, Norden bombsight |
| Programmable Devices | Jacquard loom, Analytical engine, Harvard Mark I, Z3 |
| Second Generation (Vacuum Tubes) | Calculators | Atanasoff–Berry Computer, IBM 604, UNIVAC 60, UNIVAC 120 |
| Programmable Devices | Colossus, ENIAC, Manchester Small-Scale Experimental Machine, EDSAC, Manchester Mark 1, Ferranti Pegasus, Ferranti Mercury, CSIRAC, EDVAC, UNIVAC I, IBM 701, IBM 702, IBM 650, Z22 |
| Third Generation (Discrete transistors and SSI, MSI, LSI Integrated circuits) | Mainframes | IBM 7090, IBM 7080, IBM System/360, BUNCH |
| Minicomputer | PDP-8, PDP-11, IBM System/32, IBM System/36 |
| Fourth Generation (VLSI integrated circuits) | Minicomputer | VAX, IBM System i |
| 4-bit microcomputer | Intel 4004, Intel 4040 |
| 8-bit microcomputer | Intel 8008, Intel 8080, Motorola 6800, Motorola 6809, MOS Technology 6502, Zilog Z80 |
| 16-bit microcomputer | Intel 8088, Zilog Z8000, WDC 65816/65802 |
| 32-bit microcomputer | Intel 80386, Pentium, Motorola 68000, ARM architecture |
| 64-bit microcomputer[51] | Alpha, MIPS, PA-RISC, PowerPC, SPARC, x86-64 |
| Embedded computer | Intel 8048, Intel 8051 |
| Personal computer | Desktop computer, Home computer, Laptop computer, Personal digital assistant (PDA), Portable computer, Tablet PC, Wearable computer |
| Theoretical/experimental | Quantum computer, Chemical computer, DNA computing, Optical computer, Spintronics based computer |
Other Hardware Topics
| Peripheral device (Input/output) | Input | Mouse, Keyboard, Joystick, Image scanner, Webcam, Graphics tablet, Microphone |
| Output | Monitor, Printer, Loudspeaker |
| Both | Floppy disk drive, Hard disk drive, Optical disc drive, Teleprinter |
| Computer busses | Short range | RS-232, SCSI, PCI, USB |
| Long range (Computer networking) | Ethernet, ATM, FDDI |
Software
Software refers to parts of the computer which do not have a material form, such as programs, data, protocols, etc. When software is stored in hardware that cannot easily be modified (such as
BIOS ROM in an
IBM PC compatible), it is sometimes called "firmware" to indicate that it falls into an uncertain area somewhere between hardware and software.
Computer software
| Operating system | Unix and BSD | UNIX System V, IBM AIX, HP-UX, Solaris (SunOS), IRIX, List of BSD operating systems |
| GNU/Linux | List of Linux distributions, Comparison of Linux distributions |
| Microsoft Windows | Windows 95, Windows 98, Windows NT, Windows 2000, Windows XP, Windows Vista, Windows 7 |
| DOS | 86-DOS (QDOS), PC-DOS, MS-DOS, DR-DOS, FreeDOS |
| Mac OS | Mac OS classic, Mac OS X |
| Embedded and real-time | List of embedded operating systems |
| Experimental | Amoeba, Oberon/Bluebottle, Plan 9 from Bell Labs |
| Library | Multimedia | DirectX, OpenGL, OpenAL |
| Programming library | C standard library, Standard Template Library |
| Data | Protocol | TCP/IP, Kermit, FTP, HTTP, SMTP |
| File format | HTML, XML, JPEG, MPEG, PNG |
| User interface | Graphical user interface (WIMP) | Microsoft Windows, GNOME, KDE, QNX Photon, CDE, GEM, Aqua |
| Text-based user interface | Command-line interface, Text user interface |
| Application | Office suite | Word processing, Desktop publishing, Presentation program, Database management system, Scheduling & Time management, Spreadsheet, Accounting software |
| Internet Access | Browser, E-mail client, Web server, Mail transfer agent, Instant messaging |
| Design and manufacturing | Computer-aided design, Computer-aided manufacturing, Plant management, Robotic manufacturing, Supply chain management |
| Graphics | Raster graphics editor, Vector graphics editor, 3D modeler, Animation editor, 3D computer graphics, Video editing, Image processing |
| Audio | Digital audio editor, Audio playback, Mixing, Audio synthesis, Computer music |
| Software engineering | Compiler, Assembler, Interpreter, Debugger, Text editor, Integrated development environment, Software performance analysis, Revision control, Software configuration management |
| Educational | Edutainment, Educational game, Serious game, Flight simulator |
| Games | Strategy, Arcade, Puzzle, Simulation, First-person shooter, Platform, Massively multiplayer, Interactive fiction |
| Misc | Artificial intelligence, Antivirus software, Malware scanner, Installer/Package management systems, File manager |
Programming languages
Programming languages provide various ways of specifying programs for computers to run. Unlike
natural languages, programming languages are designed to permit no ambiguity and to be concise. They are purely written languages and are often difficult to read aloud. They are generally either translated into
machine code by a
compiler or an
assembler before being run, or translated directly at run time by an
interpreter. Sometimes programs are executed by a hybrid method of the two techniques. There are thousands of different programming languages—some intended to be general purpose, others useful only for highly specialized applications.
Programming languages
| Lists of programming languages | Timeline of programming languages, List of programming languages by category, Generational list of programming languages, List of programming languages, Non-English-based programming languages |
| Commonly used Assembly languages | ARM, MIPS, x86 |
| Commonly used high-level programming languages | Ada, BASIC, C, C++, C#, COBOL, Fortran, Java, Lisp, Pascal, Object Pascal |
| Commonly used Scripting languages | Bourne script, JavaScript, Python, Ruby, PHP, Perl |
Professions and organizations
As the use of computers has spread throughout society, there are an increasing number of careers involving computers.
Computer-related professions
| Hardware-related | Electrical engineering, Electronic engineering, Computer engineering, Telecommunications engineering, Optical engineering, Nanoengineering |
| Software-related | Computer science, Desktop publishing, Human–computer interaction, Information technology, Information systems, Computational science, Software engineering, Video game industry, Web design |
The need for computers to work well together and to be able to exchange information has spawned the need for many standards organizations, clubs and societies of both a formal and informal nature.
Organizations
| Standards groups | ANSI, IEC, IEEE, IETF, ISO, W3C |
| Professional Societies | ACM, AIS, IET, IFIP, BCS |
| Free/Open source software groups | Free Software Foundation, Mozilla Foundation, Apache Software Foundation |









 Kuala Lumpur Time
Kuala Lumpur Time